We are a team of technology experts who are passionate about what we do. We LOVE our customers. We LOVE technology. We LOVE helping you grow your business with technology.
- Services
-
Al and Machine Learning
-
Artificial Intelligence Services
-
Machine Learning Services
-
Generative Al Services
-
Robotic Process Automation
-
Natural Language Processing
-
Chatbot Development Services
-
Enterprise AI Services
-
Data Annotation Services
-
MLOps Services
-
IoT Services
-
Data Mining Services
-
Computer Vision Services
-
LLM Development Services
-
-
Agents
-
AI Agents
-
Agentic AI Development
-
-
Software Development
-
Custom Software Development
-
Enterprise Software Solutions
-
Software Development Services
-
Website Development Services
-
Software Product Development Services
-
SaaS Development Services
-
-
Mobile App Development
-
Mobile App Development Services
-
Custom Mobile App Development
-
IOS App Development
-
Android App Development
-
Enterprise Mobile App Development
-
Hybrid App Development
-
-
Outsourcing
-
Software Development Outsourcing
-
Dedicated Development Team
-
Staff Augmentation Services
-
IT Outsourcing Services
-
-
BI and Data Analytics
-
Data Analytics Services
-
Data Analytics Consulting Services
-
Business Intelligence Solutions
-
-
Software Modernization
-
Software Modernization
-
Application Modernization Services
-
Legacy System Modernization
-
-
Cyber Security
-
IT Security Solutions
-
Cyber Security Solutions
-
Cyber Security Managed Services
-
HIPAA Compliance Cyber Security
-
-
Cloud Computing
-
Cloud Application Development
-
Custom Web Application Development
-
Cloud Consulting Services
-
AWS Cloud Consulting Services
-
Enterprise Cloud Computing
-
Azure Cloud Migration Services
-
- Solutions
-
AI 10X Accelerator
-
ConstructionAI
- Industries
-
Construction
-
Health Care
-
Financial
-
Real Estate
-
Manufacturing
-
Retail
-
Automotive
-
All Industries
- Pricing
- Company
-
About Us
-
Our Team
-
Testimonials
-
Awards and Recognitions
-
Careers
- Resources
-
Blog
-
eBooks
-
Case Studies
HIPAA Compliance Cyber Security
We Strengthen Your Data Security and Ensure Privacy of Sensitive Health Information by Enforcing a Robust HIPAA Compliance Cyber Security Framework.
-

We fully Implement HIPAA Procedures
-

We Run Thorough Risk Analysis of PHI
-

We Recommend Best Security Practices
-

We Strengthen Cyber Security Protocols

We are a Reliable Partner in Bolstering HIPAA Compliance Cyber Security for Fortune 500 Companies, SMBs, and Startups
Trusted by
Industry Leaders
Industry Leaders
Our Range of HIPAA Compliance Cybersecurity Services
Businesses (covered entities) are mandated to secure sensitive Public Health Information (PHI) as per HIPAA guidelines. Amidst cybersecurity challenges, we ensure complete fortification of sensitive health information handled by your organization.
Securing PHI
We provide a robust framework to tighten your data security infrastructure. We conduct a thorough assessment to identify the risks of PHI breach. We then develop an action plan to mitigate any risks, fill security gaps, and address vulnerabilities.
Securing PHI
We provide a robust framework to tighten your data security infrastructure. We conduct a thorough assessment to identify the risks of PHI breach. We then develop an action plan to mitigate any risks, fill security gaps, and address vulnerabilities.
Encrypting Sensitive Data
We eliminate unauthorized access to sensitive PHI by building a secure data encryption framework. We offer complete safeguard of sensitive information with our end-to-end encryption both in transit and at rest.
Evaluating Security Levels of Software Apps & IT System
We evaluate your application code and ensure your software applications are safe and secure from malicious attacks. We do this by redesigning application logic in a way that it prevents cyberattacks. We run a complete risk assessment to identify potential risks faced by your network and information systems and suggest methods to overcome them.
Developing Software to Comply with HIPAA
We meticulously build custom software in line with HIPAA guidelines. We apply industry best practices to ensure complete security by enabling access control, transmission security and user authentication among safety measures. We also conduct software testing and QA in line with HIPAA guidelines.
Develop and Implement Security Policies
We develop comprehensive HIPAA-compliant policies that ensure data security. We create elaborate procedures and provide complete guidance for your staff. We also implement Role-Based Access Controls for accessing PHI and enable Multi-Factor Authentication.
Promote and Assess HIPAA Compliance Awareness
With increased cyber security challenges, it is essential for business stakeholders to be aware of data security and HIPAA provisions that safeguard sensitive health information. We ensure this by providing comprehensive training to business associates and staff, and put in place an efficient training mechanism.
Comprehensive Risk Assessment
We conduct an in-depth examination of your organization’s ability to address cyber security threats in relation to HIPAA guidelines. We run comprehensive assessments of all systems that handle PHI and pinpoint their vulnerability. We also review current security measures in place and identify the risk-zones and areas of non-compliance. Our detailed cybersecurity framework addresses all compliance gaps and security risks.
Compliance Management
We guarantee your organization is in compliance with HIPAA guidelines by conducting internal audits at regular intervals. We implement the best Audit Trail practices to maintain detailed user log activity to systems having PHI access. We extend complete support to prepare for OCR audits by conducting mock audits and document reviews.
In 2024 alone, health information of 276,775,457 individuals were compromised, which is 758,288 individuals’ health information per day. - The HIPAA Journal

Why Reinforce Your HIPAA Compliance Cybersecurity with Tech.us?
Tech.us strengthens your organization’s cybersecurity landscape in line with HIPAA guidelines. We offer robust HIPAA compliance services that ensemble technical as well as administrative HIPAA requirements.
25+ Years of Expertise
With our long stint in the cybersecurity industry, we have come across an array of cybersecurity challenges across multiple dimensions and successfully overcome them. We have long experience in successfully enabling organizations to comply with HIPAA guidelines and fortifying their cybersecurity systems.
Driven by Agility
We put great emphasis on being agile, which is our primary culture. We deliver resilient HIPAA compliance cybersecurity solutions to your changing needs. We value the organizations’ data security and place effective cybersecurity measures in place.
Global Reach
We follow a global delivery model, which is flexible and robust. With that, we extend continuous support to your business - any time, any place. We guarantee your business deliverables match with your local as well as global needs through our seamless collaboration.
Maximum Value for
Your Investment
We mitigate potentially costlier cybersecurity risks and hefty HIPAA non-compliance fines by enabling robust cybersecurity measures. We help you cut unnecessary costs and enable you to channel your resources to other useful areas with our efficient services.
1500
+
PROJECTS COMPLETED
25
+
YEARS IN
BUSINESS
30
+
INDUSTRIES
SERVED
2
X
Up to 2X faster
time to Market
100
%
COMMITMENT TO
YOUR SUCCESS
5
Continents
Served
Industries We’ve Worked Together
The rise in technological advancements poses imminent cybersecurity threats to healthcare and pharmaceutical organizations. Compliance with HIPAA guidelines ensures the secure data handling practices of organizations. We help them build reliable HIPAA compliance cybersecurity solutions.
Healthcare
Companies
Healthcare Software
Product Companies
Medical Equipment
Manufacturers
Pharmaceutical
Companies
Tech Stack
We leverage our decade-long expertise to handpick the best stack of technology tools for strengthening HIPAA Compliance Cybersecurity.
AI / ML



























Frontend











Backend







iOS








Android







Database








Cloud & DevOps












AI / ML



























Frontend












Backend







iOS








Android








Database








Cloud & DevOps












The Success Stories of Our Clients
We value data privacy and security of sensitive health information and help organizations protect themselves from cybersecurity challenges. Here are the success tales of our partners.

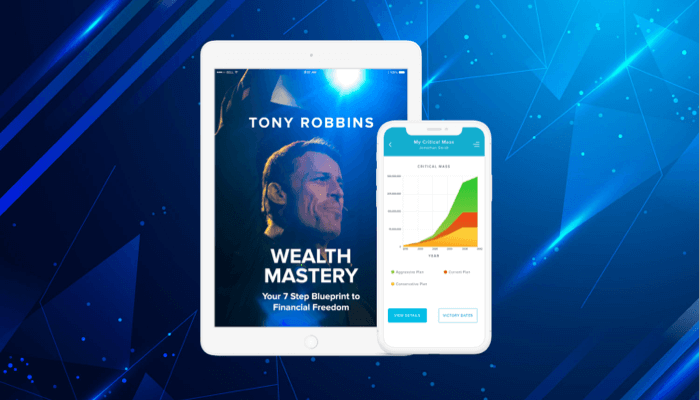
Helping millions of people achieve ultimate financial freedom in life. Tony Robbin’s ‘Wealth Maestry’ - An application that provides wealth management solutions & tools to achieve financial success.
Results
Customer Satisfaction
- Personalized financial plans with robust tech support
Boosted ROI
- Increase revenue through continuous support

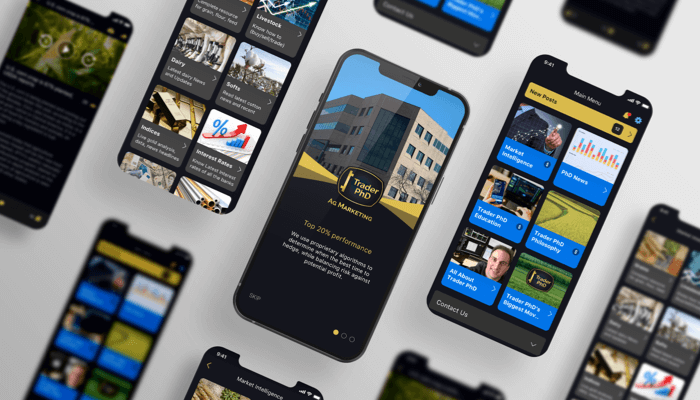
Redefining the face of agriculture and helping farmers make informed choices in the commodity market. Trader PhD’s mobile app provides real-time market data, analysis tools, and expert insights to help farmers maximize their profits.
Results
+ $2 Million
- Increase Annual Revenue
Increased Monetization and Decreased Friction
- Through easy in-app purchases and targeted advertising

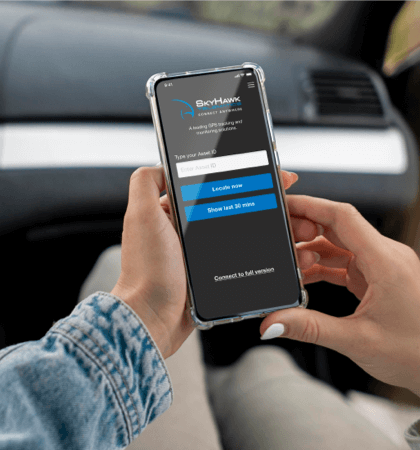
SkyHawk by Telus created a lightweight mobile version of their Connect Anywhere application which provides fleet connectivity & operational excellence. We built various features including locating assets, fleet activity, secure configurations & a lot more in a seamless mobile interface.
Results
Improved Digital Experience
- Enhanced experience with seamless map display
Increased Revenue
- Improved returns through better functionality


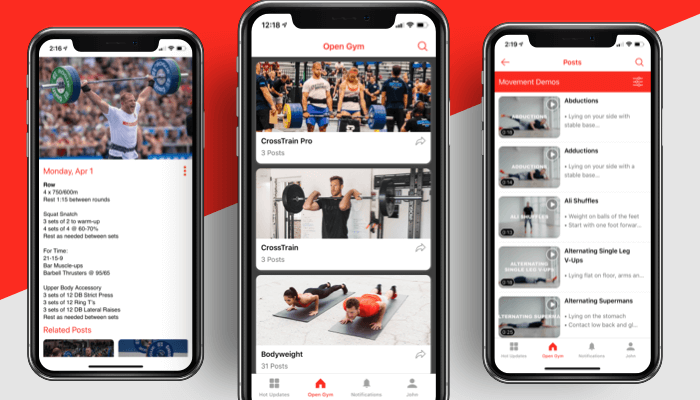
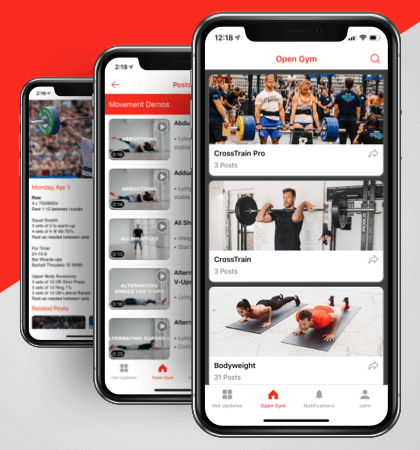
Making world class training easy and accessible with a seamless, intuitive mobile app. Partnering with Tech.us, Open Gym created a first-of-its-kind fitness application that simplifies the fitness game and includes in-app purchase functionalities.
Results
50% Boost
- Achieved in business
Real-Time Updates
- Implemented timely information dissemination
Awards & Recognitions
We at Tech.us are driven by shared values: to be a reliable and skilled team of experts. The awards we received further underscore our core values.





What Will You Gain from Our HIPAA Compliance Cybersecurity Service?
Organizations in compliance with HIPAA guidelines are typically known to be having higher credibility and reliability. Besides, HIPAA Compliance Cybersecurity ensures complete protection and saves costs.

Stay Up-to-Date
We help you stay informed about HIPAA guidelines and regulatory updates.
Fill Gaps
We identify and resolve compliance gaps by leveraging our technological & domain expertise.
Breach Alerts
We engineer response plans for each specific breach and enable prompt breach alerts.
Assess Risk
We examine the security breach or compliance gaps. We identify vulnerabilities in the system and any risks to PHI and then assess the risks associated.
Ongoing Monitoring
We put in place a continuous monitoring mechanism to ensure your organization’s compliance with HIPAA guidelines.
Common Queries about HIPAA Compliance Cybersecurity
Find answers to the commonly asked questions about our HIPAA compliance cybersecurity
To be compliant with HIPAA guidelines enables an organization to be trustworthy. It increases the company’s reliability and boosts the loyalty of patients, who can rest assured that their sensitive health information is in a secure place.
HIPAA compliance ensures better data security. It further enables organizations to manage cybersecurity breaches proactively.
Primarily, the following categories of organizations should be HIPAA-compliant:
Covered Entities:
Companies that are closely associated with healthcare operations come under this category. It predominantly includes healthcare organizations and insurance companies that have access to PHI.
Business Associates:
HIPAA also mandates “business associates” to comply with its guidelines. They are the organizations that have access to PHI and provide services to covered entities. To be more clear, if a company handles billing of a hospital and has access to data such as patient’s name, address, etc., then that company falls under the category of business associates.
Normally, a break in PHI would amount to HIPAA violation. Below are some common instances that constitute as HIPAA violations:
- Lost or stolen devices
- Malware and Ransomware
- Accidentally sharing sensitive data via social media, email, etc.
- Break-in to the office physically
- Violation of Electronic Health Records
- When user credentials are compromised
To stay compliant with HIPAA, a combined effort of cybersecurity and IT security solutions is must.
It is important to note that not all health information is considered as PHI. Some information such as employee health records do not come under PHI. Hence sharing such information does not count as a violation of HIPAA guidelines.
In some cases, sharing PHI does not count as violation as this is justified. Sharing health information of patients with them, or sharing PHI between healthcare providers for treating the patient do not constitute violation of HIPAA rules.
To be more specific on what and what not constitute violations under HIPAA rules, we recommend to run through the detailed HIPAA Compliance Rules.


Our Services
Talk to US
© 2024 Tech.usTM. All Rights Reserved.


