We are a team of technology experts who are passionate about what we do. We LOVE our customers. We LOVE technology. We LOVE helping you grow your business with technology.
- Services
-
Al and Machine Learning
-
Artificial Intelligence Services
-
Machine Learning Services
-
Generative Al Services
-
Robotic Process Automation
-
Natural Language Processing
-
Chatbot Development Services
-
Enterprise AI Services
-
Data Annotation Services
-
MLOps Services
-
IoT Services
-
Data Mining Services
-
Computer Vision Services
-
LLM Development Services
-
-
Agents
-
AI Agents
-
Agentic AI Development
-
-
Software Development
-
Custom Software Development
-
Enterprise Software Solutions
-
Software Development Services
-
Website Development Services
-
Software Product Development Services
-
SaaS Development Services
-
-
Mobile App Development
-
Mobile App Development Services
-
Custom Mobile App Development
-
IOS App Development
-
Android App Development
-
Enterprise Mobile App Development
-
Hybrid App Development
-
-
Outsourcing
-
Software Development Outsourcing
-
Dedicated Development Team
-
Staff Augmentation Services
-
IT Outsourcing Services
-
-
BI and Data Analytics
-
Data Analytics Services
-
Data Analytics Consulting Services
-
Business Intelligence Solutions
-
-
Software Modernization
-
Software Modernization
-
Application Modernization Services
-
Legacy System Modernization
-
-
Cyber Security
-
IT Security Solutions
-
Cyber Security Solutions
-
Cyber Security Managed Services
-
HIPAA Compliance Cyber Security
-
-
Cloud Computing
-
Cloud Application Development
-
Custom Web Application Development
-
Cloud Consulting Services
-
AWS Cloud Consulting Services
-
Enterprise Cloud Computing
-
Azure Cloud Migration Services
-
- Solutions
-
AI 10X Accelerator
-
ConstructionAI
- Industries
-
Construction
-
Health Care
-
Financial
-
Real Estate
-
Manufacturing
-
Retail
-
Automotive
-
All Industries
- Pricing
- Company
-
About Us
-
Our Team
-
Testimonials
-
Awards and Recognitions
-
Careers
- Resources
-
Blog
-
eBooks
-
Case Studies
IT Security Solutions
We Provide Robust Security Measures to your Entire IT Infrastructure
-

We Help you Achieve 100% Resilience against Security Risks
-

We Ensure Zero Compromise on your Organization’s Reputation
-

We Employ Extensive Protection with the Latest IT Security Tools
-

We Offer Proactive & Affordable IT Security Solutions
.png)
We are a Reliable Partner in Bolstering the Security of IT Infrastructure for Fortune 500 Companies, SMBs, and Startups
Trusted by
Industry Leaders
Industry Leaders
IT Security Solutions We Provide
With increased reliance on digitalization, securing digital assets – data, network, and other digital infrastructure – is important, we help you safeguard them. Our IT security solutions extend beyond protecting your digital infrastructure, we provide effective measures to secure your entire IT infrastructure – cloud, network, systems & devices – from eternal as well as internal threats.
Network Security
We strengthen your network systems, our expert team averts any unauthorized access to your network resources. We employ different technologies and proven methods to safeguard your network infrastructure – enable multi-factor authentication, VPN encryption, etc., our team also segments your network infrastructure to inhibit the malware spread.
Network Security
We strengthen your network systems, our expert team averts any unauthorized access to your network resources. We employ different technologies and proven methods to safeguard your network infrastructure – enable multi-factor authentication, VPN encryption, etc., our team also segments your network infrastructure to inhibit the malware spread.
Cloud Security
The growing dependency on cloud environments – be it SaaS, PaaS, or IaaS – poses security challenges, especially from cyberattacks. Our team uses a set of defined procedures, we address security threats and ensure your cloud applications, be it SaaS products or custom developed applications, as well as cloud infrastructure, are safe.
Endpoint Security
Our comprehensive security approach ensures safety of your organization’s end-point devices – computers, mobile phones, servers, and so on – cyberattacks mainly target endpoint devices to gain access to sensitive information. We employ advanced technology, our team prevents cybercriminals from accessing endpoint devices, as we block network access without disrupting regular operations.
Internet Security
Our robust internet security measures protect your sensitive information – usernames, passwords, bank/financial details, other sensitive details – that are stored in browsers and other internet applications. We employ a broader scope of security measures, our methodologies prevent or rectify the Denial of Service attacks, DoS, we effectively remove malware that may cripple your systems.
IoT Security
IoT devices are generally vulnerable to cyberattacks, our experienced team strengthens the security framework as we employ advanced security tools and procedures. API security, public key infrastructure (PKI) authentication, encryption techniques are some common methods, with technologies and similar methods, we help prevent cybercriminals from accessing network through IoT devices.
Vulnerability Management
With solid and proven security methods, we assess your IT systems, our team checks for weak points that may make your system vulnerable to security threats. We do continuous assessments of all your systems, networks, as well as enterprise applications, we employ thorough evaluation and reporting on any vulnerabilities.
Application Security
Our application security measures involve securing hardware systems as well as software applications, our team ensures code or app data remain unaffected in the event of cyberattacks. We help you to protect applications, our team employs safety measures in coding to protect apps from future threats, then precisely identifies security gaps within the existing software.
Why Secure Your IT Infrastructure with Tech.us?
Tech.us strengthens your organization’s It infrastructure, our team ensures your organization complies with necessary regulations in place. We offer robust IT security solutions that comprise robust technical as well as administrative methodologies.
Decade-Long Expertise
We have a long industrial stint in digital landscape, this enables us to have a real-time experience in dealing with security threats of various complexities. With evolving IT landscapes, security challenges are also evolving, so are our technologies in effectively addressing them.
Faster Solutions
Our emphasis on being agile enables us to deliver IT security measures, we help your organization to remain resilient against external as well as internal threats to IT infrastructure. We value your organization’s security, our methodologies help you function efficiently at all times.
Proven Record
We have secured our credibility from our clients for having effectively secured their IT infrastructures, the list comprises Fortune 500 companies as well as startups. With successful delivery of more than 1,500+ projects, our team makes us a trusted partner in five continents.
Strengthens Reputation
A security breach of any scale – be it cyberattack, data theft, or other breaches – destabilizes the reputation of an organization, sometimes it may have to pay exorbitant penalties, in case of non-compliance. We eliminate this scenario, our robust security measures ensure complete protection.
1500
+
PROJECTS COMPLETED
25
+
YEARS IN
BUSINESS
30
+
INDUSTRIES
SERVED
2
X
Up to 2X faster
time to Market
100
%
COMMITMENT TO
YOUR SUCCESS
5
Continents
Served
Our Effective, Efficient & Expert Practices
Partner with Tech.us and redefine your IT security, we help you protect your IT infrastructure, better understand the challenges, then develop security solutions required to your business.
Understand
Explain your safety requirements, we work alongside you, our team understands the objectives as well as assesses your current security measures.

Cost Estimate
Our budget estimates are transparent when it comes to resource allocation for security measures, we clearly inform you the required investments.

Plan
We come up with a clear roadmap to deliver IT security solutions, once you approve it, we initiate our work.

Deliver
We employ robust security measures, they are in line with industry best practices, our solutions are precise and timely.
Tech Stack
Evolving security challenges require advanced technology and tools, our team employs the best-in-class technology to address the issues effectively.
AI / ML



























Frontend











Backend







iOS








Android







Database








Cloud & DevOps












AI / ML



























Frontend












Backend







iOS








Android








Database








Cloud & DevOps












Success Stories
Our clients trust us with the safety of IT systems and infrastructure, we partner with them through our robust safety measures to secure their organizations.

Helping millions of people achieve ultimate financial freedom in life. Tony Robbin's 'Wealth Maestry' - An application that provides wealth management solutions & tools to achieve financial success.
Results
Customer Satisfaction
- Personalized financial plans with robust tech support
Boosted ROI
- Increase revenue through continuous support

Redefining the face of agriculture and helping farmers make informed choices in the commodity market. Trader PhD’s mobile app provides real-time market data, analysis tools and expert insights to help farmers maximize their profits.
Results
$2 Million
- Increase Annual Revenue
Increased Monetization and Decreased Friction
- Through easy in-app purchases and targeted advertising

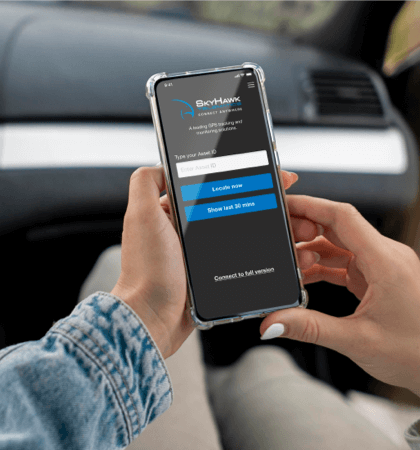
SkyHawk by Telus created a lightweight mobile version of their Connect Anywhere application which provides fleet connectivity and operational excellence. We built various features including locating assets, fleet activity, secure configurations and a lot more.
Results
Improved Digital Experience
- Enhanced experience with seamless map display
Increased Revenue
- Improved returns through better functionality


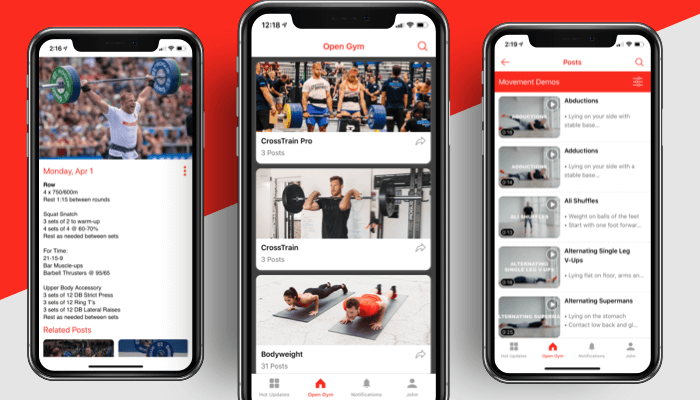
Making world-class training easy and accessible with a seamless and intuitive mobile app. Partnering with Tech.us, Open Gym created a first-of-its-kind fitness application that simplifies the fitness game and also has in-app purchase functionalities.
Results
50% Boost
- Achieved in business
Real-Time Updates
- Implemented timely information dissemination
Our Solutions for IT Security Threats
Although cyberthreat is common, many security challenges are there that affect organizations’ workflow as well as reputation, we employ unique solutions to different security threats.

Malware Threats
Malware is a collection of malicious software, they inhibit normal functioning of infected systems. Our security measures prevent malware, be it any kind, from accessing, encrypting, or deleting data.
Our IT security measures extend to:
- Ransomware
- Spyware
- Trojan horse
- Worm & Virus

Social Engineering Threats
A mix of practices used to persuade people and trick them into sharing sensitive information – passwords, financial data, sensitive files and folders – constitutes social engineering threats. Our elaborate IT security solutions are catered to tackle such threats.
Our measures address:
- Phishing of all types
- Business Email Compromise – BEC
- Spam Detection

DoS Attacks
It is Denial of Service attacks - unique security threat, cybercriminals cripple a website or application by driving enormous fraudulent traffic. It affects its performance, and legitimate users are unable to access it. Our IT security solutions provide firm protection from DoS attacks.
We secure you against:
- Denial of Service – Dos
- Distributed Denial of Service – DDoS


Industry Partners
Safeguarding IT infrastructure – organizations’ network and cloud platforms, IT systems, data & information – is crucial, our solutions enable better security to organizations across industries.
Healthcare
Fintech
Retail &
Supply Chain
Insurance
Logistics &
Transportation
Manufacturing
Energy
Professional
Services
Real-Estate &
Construction
Telecommunication
Awards & Recognitions
Our industry awards & recognitions stand as a proof to our excellence in securing companies’ IT infrastructure with our proof-tested solutions.


.png)


IT Security Practices Tech.us Employs
Threats to digital assets and IT systems are proliferating, we follow the best industry practices when it comes to IT security, our solutions enforce strict adherence to compliance and protocols.

Multi-factor authentication
It is a basic yet effective way to keep your systems, applications as well as network safe, we adopt multiple secure credentials and use complex patterns to protect passwords.
Incident Response
We utilize this approach to make cybersecurity teams be prepared, our detailed incident response plan helps to prevent cyberattacks before they occur.
Awareness Training
Our security awareness training equips your employees with necessary procedures to follow – to prevent as well as to address challenges – we train them against phishing, how to apply authentication, best practices to follow, and so on.
Commonly Asked Questions
Find answers to the commonly asked questions about our IT Security Solutions
IT security solution is a broad aspect of securing entire IT infrastructure – network, software applications, cloud platforms, data and information, cyberspace, websites, physical systems like computers, mobile phones, and so on. Some common IT security solutions comprise:
- Network Security
- Application Security
- Data & Information Security
- Cybersecurity
- Cloud Security
- Email Security
- Identity & Access Management
With increased dependency on digital platforms as well as evolving threat landscape, more and more organizations are susceptible to IT security threats, this necessitates a robust security framework that encompasses all IT assets. Businesses have much to lose from a security breach, this is along with valuable assets, their reputation is put at stake, hence comprehensive IT security solutions are crucial.
It security threats encompass a wide range of security issues, they include threats to network, cloud, software, and so on.
- Malware – spyware, ransomware, etc.
- Phishing emails, SMS, WhatsApp messages
- Data and information breaches
- Denial of Service attacks
- Trojan horse
- Viruses
- Inside threats


Our Services
Talk to US
© 2024 Tech.usTM. All Rights Reserved.


